Applications are invited for Certificate Course On Cyber Security And Digital Forensics at IIIT Pune on 4 Dec 2023- 3 Jan 2024. The last date of registration is 30 September.
Course Overview
This course is aimed at training cybersecurity professionals in identifying and reporting the security bugs, especially those related to security exploits and vulnerabilities in a legal and ethical manner. The course allows one to upscale and pursue a career in challenging, adventurous and rewarding field of bug bounty research with hands on experience.
The proposed program is an Instructor-led program that covers essential training on cyber security and digital forensic investigation techniques. The course provides knowledge of real-world scenarios with hands-on experience on case studies to develop forensic skills.
The course delves into the concepts of forensic investigation, security, volatility framework, autopsy, scalpel, Nmap, DNS pharming, DoS attack, session high jacking, hashcat, etc. that are essential to become an advanced cybersecurity professional.
The proposed program is designed to equip students and professionals aspiring to start a technical career in cyber security. This is a technical skilling program, essential to launch a professional career in the exciting domain of Cyber Security and Digital Forensics.
Course Highlight
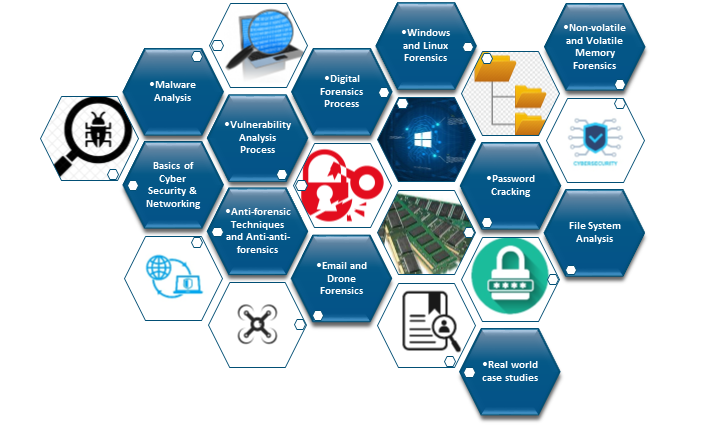
Course Modules
Module-1: Basics of Cyber Security
- Security Goals: Confidentiality, integrity, and availability,
- Authentication, Authorization and, Auditing.
- Information security risk management.
Module-2: Basics of Networking
- OSI/TCP
- Networking devices and security equipments
- Protocols
- Subnetting and super netting
- Cryptography and hashing
Module-3: Vulnerability Analysis Process, Tools and Techniques
- Active & Passive Foot-printing,
- Protocol Analyzers and Port Scanners,
- OS Fingerprinting,
- Vulnerability Scanners.
Module-4: Malware and Static & Dynamic Analysis
- Social engineering
- Malicious logic, Trojan horses, viruses.
- Boot sector and executable infectors.
- Spyware, adware, and ransomware.
Module-5: Securing Linux System: Access Control mechanism
- Discretionary access control
- Mandatory access control
- Role-based access control
- Linux permission model
- Shadow and password file
Module-6: Digital Forensics: Process, Tools & Techniques and Research Challenges
- Definition of Digital Forensics
- Disk Drives and their characteristics
- Understanding Hard Disk Partitions
- Booting Process in different Operating Systems
- Slack Space
- Forensics Imaging
- Imaging using FTK Imager
Module-7: Understanding Hard Disks and File Systems (NTFS & Ext4)
- Disk Drives and their characteristics
- Understanding Hard Disk Partitions Booting Process in different Operating Systems
- Slack Space
- Metadata in NTFS and Ext4 file systems
Module-8: Data Acquisition: Imaging and Cloning
- Hashing and Write Blockers
- Forensics Imaging in Kali Linux using dd, dcfldd, dc3dd
- Imaging using FTK Imager
Module-9: File Systems Analysis using TSK
- Analyzing disk images using TSK utilities
Module-10: Windows Forensics
- Registry Forensics
- Recycle Bin Forensics
- Jump List Forensics
- SRUDB.dat forensics
- Prefetching in Windows
- Program Executions Artifacts
Module-11: Anti-forensics and Anti-anti-forensics
- Data Hiding into Slack Space
- Secure Deletion
- Timestomping
Module-12: Volatile Memory Forensics
- Why/What Memory Forensics
- Volatility Configuration
- Volatility Analysis
- Windows Memory Analysis
Module-13: Linux Forensics
- Basic Linux Commands
- File Hierarchy Standard
- Hunt Users and Groups
- File Hunting
- Failed logins and Actors IP address
- Timestamps and Deleted files in Journal
Module-14: Email and Drone Forensics
- Examining Email messages
- Email Server Examination
- Tracing emails
- Email Forensics Tools
- Introduction to Drone forensics and challenges
Module-15: Password Recovery
- Password Cracking Methods
- Password Cracking Tools
- Hashcat for Windows password cracking
Module-16: Mobile Forensics
- Phone Locks and Discuss Rooting of Android
- Mobile Forensics Process
- Perform Logical Acquisition on Android
- Perform Physical Acquisition on Android
- Mobile Forensics Challenges
- CDR Analysis
Eligibility
- UG/PG graduated students.
- Ph.D. Scholars from higher education institutes.
- Faculties / Staffs / Lab Instructors from technical and academic institutions.
- Industry/working professionals seeking cyber security skills.
- Any other Cyber Security enthusiasts.
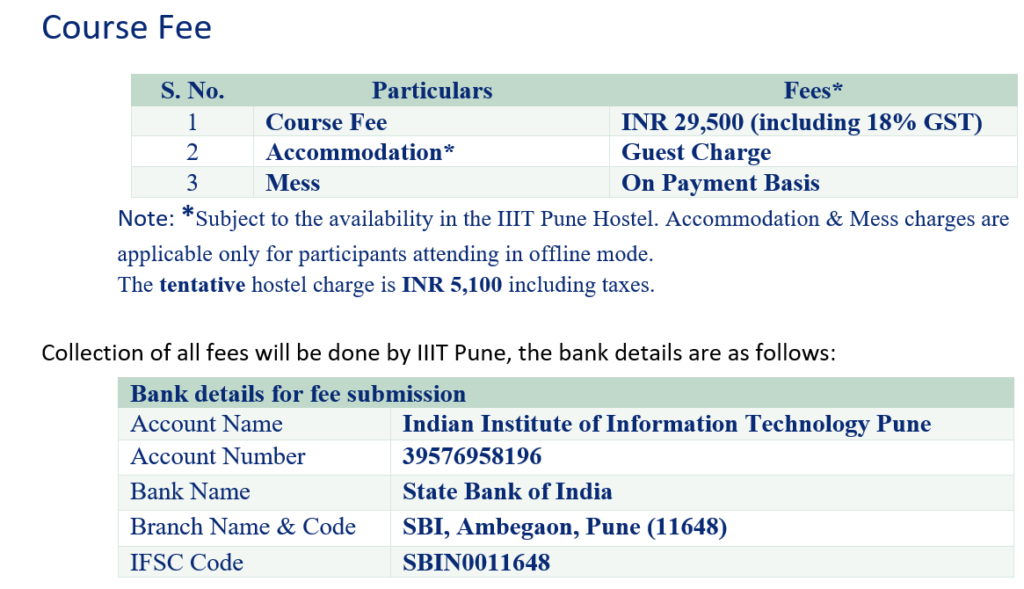
Fees
Important dates
- Application Open Date: 8th August, 2023
- Application Closure Date: 30th Sept, 2023
- Course Commencement: 4th Dec, 2023
- Course End Date: 3rd Jan, 2024
Registration
Interested candidates can register online via this page.
Learning Outcomes
- Proactively investigate complex security threats, allowing them to investigate, record, and report cybercrimes to prevent future attacks
- Identify & Evaluate Information Security threats and vulnerabilities in Information Systems and apply security measures to real time scenarios
- Identify common trade-offs and compromises that are made in the design and development process of Information Systems
- Demonstrate the use of standards and cyber laws to enhance information security in the development process and infrastructure protection.






![JEE Main 2025 Free Preparation Crash Course by IIT Kanpur [45 Days; Daily-Live Doubt Clearance Session]](https://cse.noticebard.com/wp-content/uploads/sites/23/2024/11/Featured-image-logo-2024-11-16T111958.202.jpg)